Test your employees against cyber attacks
With phishing attacks, which make up 86% of cyber attacks, hackers can steal your company's private information and sell it to your competitors.
Get Started arrow_forward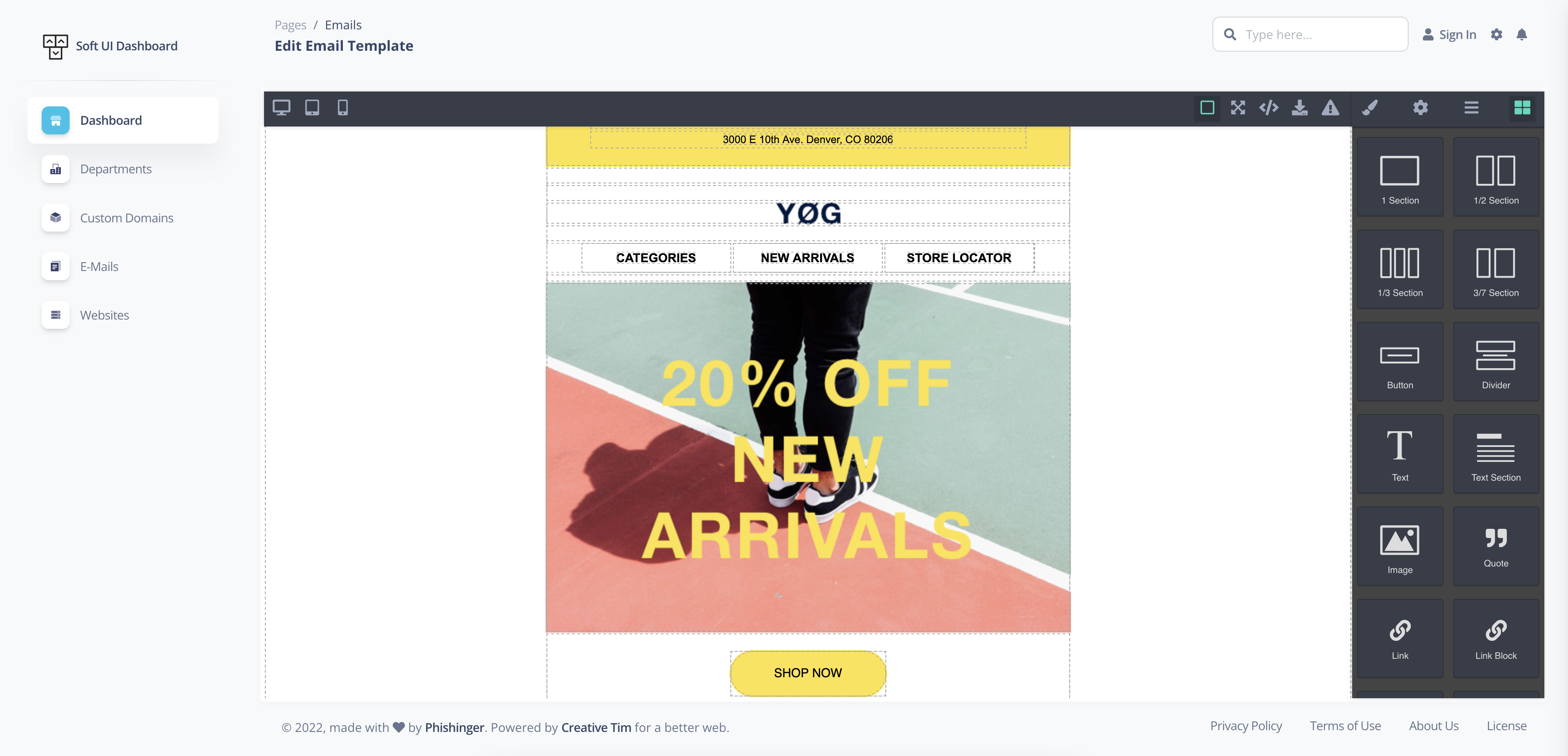




With phishing attacks, which make up 86% of cyber attacks, hackers can steal your company's private information and sell it to your competitors.
Get Started arrow_forwardPhishing is an attempt to seize sensitive information by pretending to be a reliable electronic communication tool. This sensitive information may be private information such as username, password, credit card information. Phishing is typically initiated with a fake email or other electronic media messages. It usually proceeds by redirecting users to a fake website that appears to be real, then asking them to enter their personal information.
By using Phishinger, you can take precautions against hackers by raising cyber awareness to your employees.
Get started right away with automated tests. We will send the e-mails for you and report them.
Get started right away with automated tests. We will send the e-mails for you and report them.
With our powerful editor, you can prepare special e-mails for your company.
With our powerful editor, you can prepare special e-mails for your company.
With the Cloner tool, You can clone any website you want. The Cloner will be prepare the website in you want domain.
With the Cloner tool, You can clone any website you want. The Cloner will be prepare the website in you want domain.
Test your users with different scenarios at different times for sharper results.
Test your users with different scenarios at different times for sharper results.
Realistic and spam-free phishing emails
More realistic phishing sms along with emails.
Cloned landing and login pages.
More dangerous Malware and Ransomware.